What is the 3-D Secure Protocol?
The 3-D Secure (3DS) protocol is a security standard used in the online payment industry to perform additional authentication for credit and debit card transactions. The name "3-D Secure" stands for "Three-Domain Secure," as the system involves three main domains: the acquirer domain (merchant and acquiring bank), the issuer domain (issuing bank and cardholder), and the interoperability domain (network infrastructure and servers that enable communication between the other two parties).
The main goal of 3-D Secure is to enhance the security of online payments and reduce fraud risk by verifying the cardholder’s identity during transactions. This is achieved through an additional authentication step that may include requesting further information such as a temporary security code sent to the cardholder’s mobile phone.
The 3-D Secure protocol is used and supported by the major credit and debit card networks, such as Visa, MasterCard, American Express, Discover, and Diners. Each has its own implementation of the protocol, known as Visa Secure, Mastercard Identity Check, American Express SafeKey, and ProtectBuy for both Diners and Discover.
The latest version of the protocol is 3-D Secure 2 (3DS2), which brings significant improvements in user experience, reduces friction during checkout, and offers greater flexibility and adaptability to changes in the online payment environment.
Note: "Active" means EMVCo requires testing of 3DS components. "Inactive" means no EMVCo testing support is available.
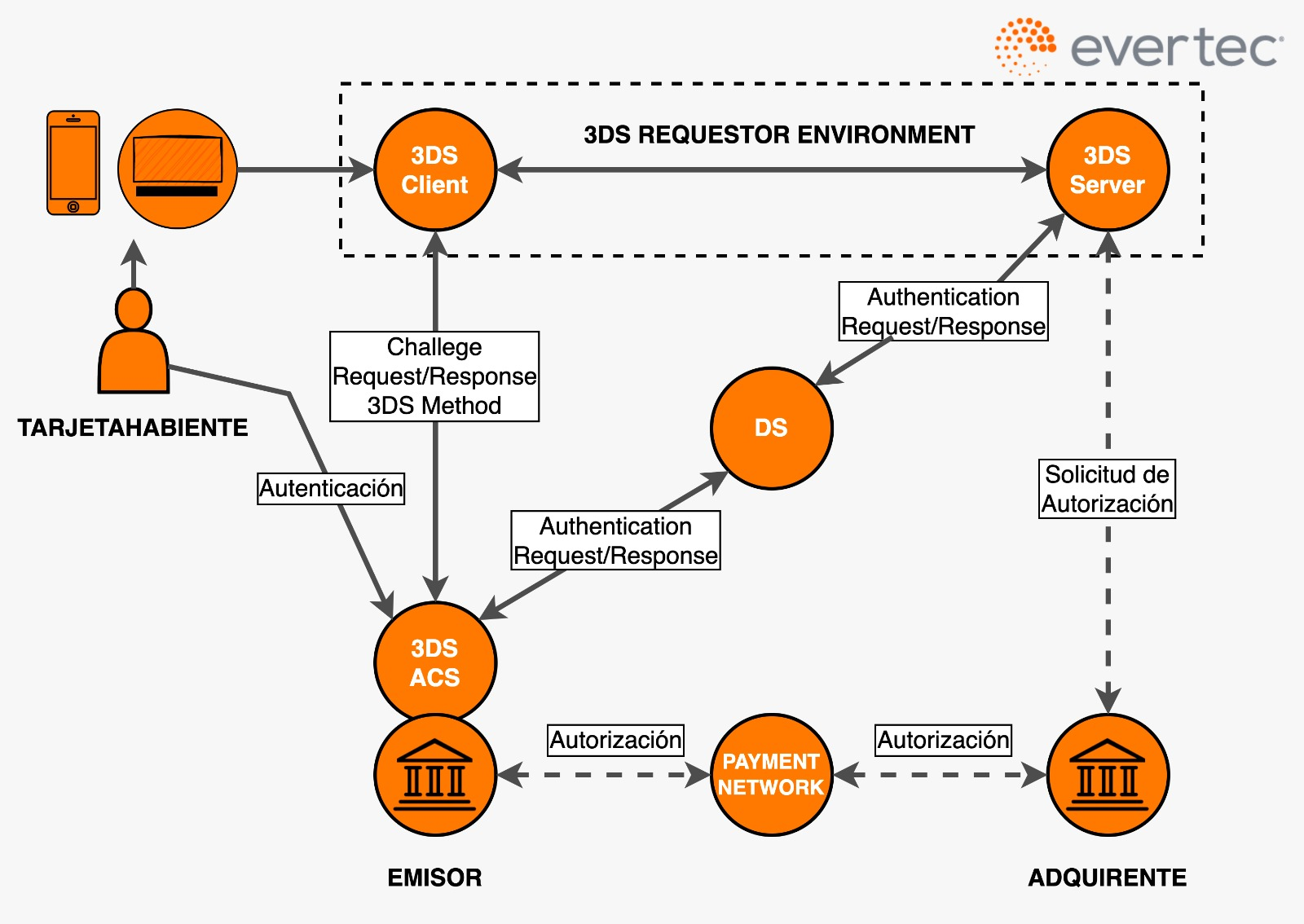
How does 3-D Secure work?
The 3D Secure (3DS) protocol works as an additional authentication layer for online transactions made with credit or debit cards.
-
Transaction Initiation: The cardholder begins an online transaction by selecting products or services on the merchant's website or app and proceeds to checkout.
-
Authentication Request: Once the cardholder enters their card details, the merchant (via the acquirer's 3DS server) sends an authentication request to the Directory Server (DS). The DS identifies the card’s issuing bank and forwards the request to the Access Control Server (ACS) of that issuer.
-
Authentication Process: The ACS evaluates the transaction's risk level. This may involve checking the cardholder’s IP address, transaction history, geographic location, etc. If the transaction is deemed low risk, it may be authenticated without cardholder involvement (frictionless authentication). If it is considered high risk, the ACS will require additional verification, such as a one-time password via SMS, security questions, or biometric authentication.
-
Authentication Result: Once the authentication process is complete, the ACS sends the result back to the acquirer’s 3DS server. The result may indicate a successful authentication, an attempted authentication, or a failed authentication.
-
Transaction Completion: The merchant receives the authentication result and proceeds to finalize the transaction. If the authentication was successful, the merchant requests payment authorization from the issuer. If approved, the transaction is completed and payment is made.
-
Confirmation: Finally, the cardholder receives confirmation of the transaction via the merchant’s website or app, or through a notification or email.
This process helps protect against the unauthorized use of credit cards online by adding an extra layer of security and authentication.
Authentication Flows
Frictionless Flow
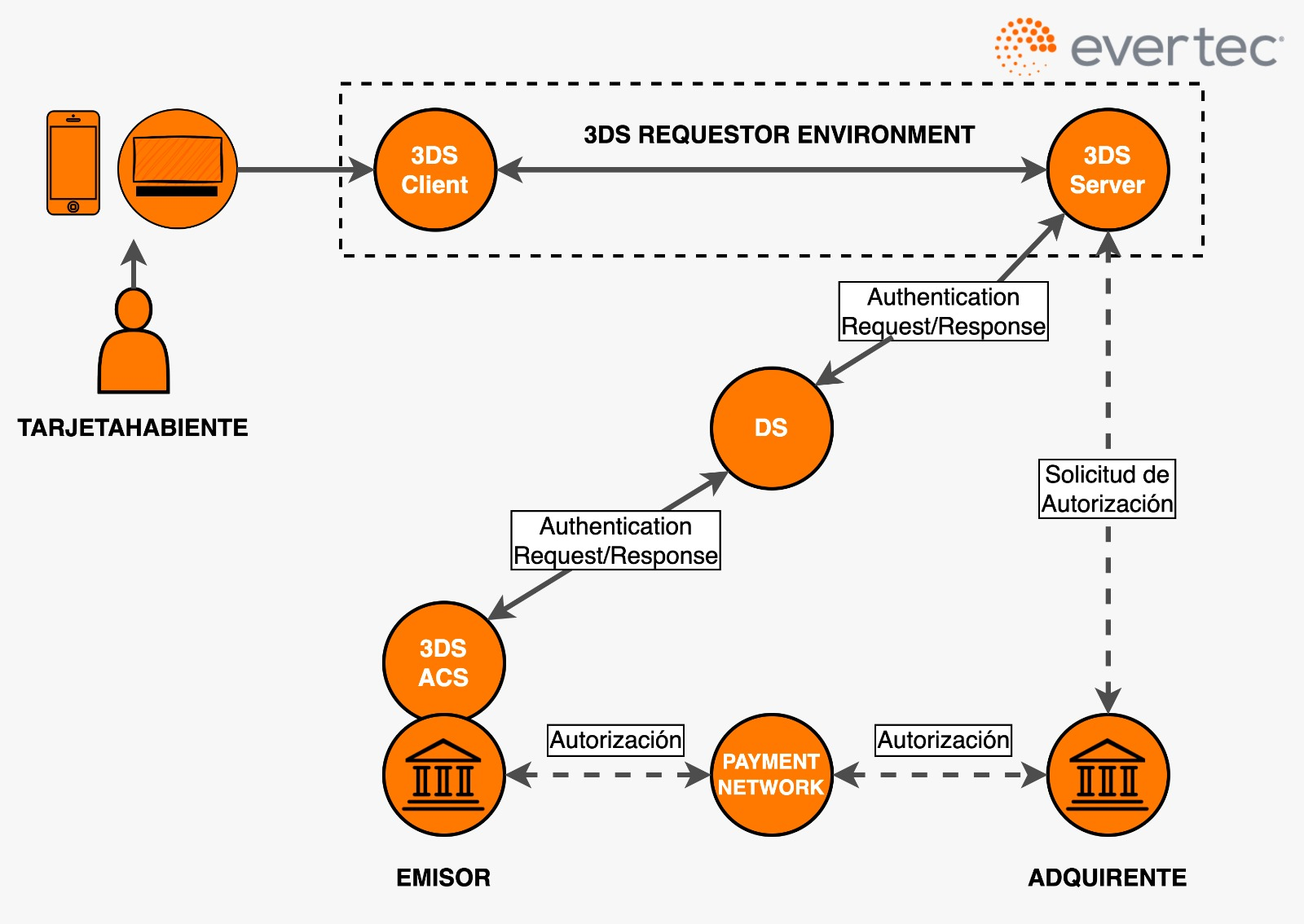
Challenge Flow